Corporations today are thinking about how to protect assets. A few of the white collar crime problems include hacking/intrusions (cyber vulnerability), insider/outsider trading (convergence of cyber and financial crimes), the Foreign Corrupt Practices Act (FCPA), spear fishing (email compromise) and economic espionage. They must consider the possibility of internal corruption or external corruption, and environmental factors such as culture and competition contributing to these crimes. As protection, organizations can use cyber security, pen testing and data loss prevention tactics.
WHAT IS CYBER SECURITY?
Cyber security is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attacks, damage or unauthorized access. The term "cyber security" refers to business function and technology tools used to protect information assets. Data is increasingly digitized and the internet is being used to save, access and retrieve vital information. Protecting this information is no longer a priority but has become a necessity for most companies and government agencies around the world.
Here are some other key definitions:
Data breaches are occurring more frequently. There are increasing pressures for businesses to step up efforts to protect personal information and prevent breaches.
Cyber criminals attack to gain political, military or economic advantage. They usually steal money or information that can eventually be monetized (e.g., Social Security numbers, credit history, credit cards, health records, etc.).
Cyber attacks may come from malicious outsiders, accidental loss, malicious insiders, hacktivists and state-sponsored actors. 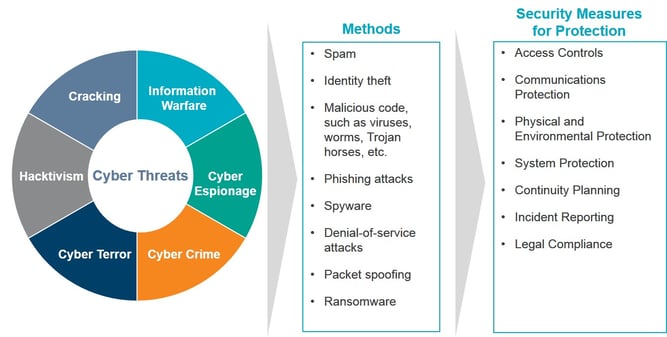
DEFINING INTERNAL AUDIT’S ROLE IN CYBER SECURITY
When it comes to selecting a cyber security control framework, guidance and frameworks don’t need to be reinvented. Organizations should choose the one that works for them (e.g., ITIL or COBIT), add onto it and take responsibility for it. Here are some of the frameworks to choose from:
- NIST Framework for Improving Critical Infrastructure Cybersecurity
- ISACA COBIT 5 and the Emerging Cyber Nexus
- SANS Institute and the Top 20 Critical Security Controls
- PCI DSS Control Catalog
- ISO/IEC 27001
- Other Industry Specific Frameworks: FFIEC, HITRUST, etc.
Cyber Risk: Roles and Responsibilities
Effective risk management is the product of multiple layers of risk defense. Internal audit should support the board in understanding the effectiveness of cyber security controls.
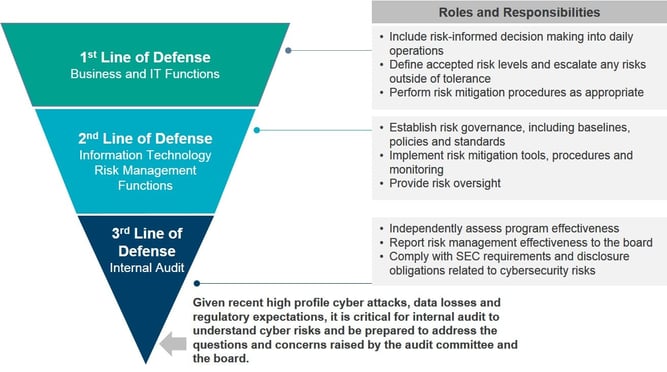
These three lines of defense for cyber security risks can be used as the primary means to demonstrate and structure roles, responsibilities and accountabilities for decision-making, risks and controls to achieve effective governance risk management and assurance.
Business operations perform day-to-day risk management activity such as risk identification and risk assessment of IT risk. They provide risk responses by defining and implementing controls to mitigate key IT risks, and reporting on progress. An established risk and control environment helps accomplish this.
Risk management is the process of drafting and implementing policies and procedures, ensuring that existing procedures are kept up to date, responding to new strategic priorities and risks, monitoring to ensure compliance with the updated policies, and providing surveillance over the effectiveness of the compliance controls embedded in the business.
As the 3rd line of defense, what steps can internal audit take?
- Work with management and the board of directors to develop a cyber security strategy and policy.
- Identify and act on opportunities to improve the organization’s ability to identify, assess and mitigate cyber security risk to an acceptable level.
- Recognize that cyber security risk is not only external; assess and mitigate potential threats that could result from the actions of an employee or business partner.
- Leverage relationships with the audit committee and board to heighten awareness and knowledge on cyber threats, and ensure that the board remains highly engaged with cyber security matters and up to date on the changing nature of cyber security risk.
- Ensure that cyber security risk is integrated formally into the audit plan.
- Develop and keep current an understanding of how emerging technologies and trends are affecting the company and its cyber security risk profile.
- Evaluate the organization’s cyber security program against the NIST Cybersecurity Framework, recognizing that because the framework does not reach down to the control level, the cyber security program may require additional evaluations of ISO 27001 and 27002.
- Seek out opportunities to communicate to management that, with regard to cyber security, the strongest preventive capability requires a combination of human and technology security—a complementary blend of education, awareness, vigilance and technology tools.
- Emphasize that cyber security monitoring and cyber incident response should be a top management priority; a clear escalation protocol can help make the case for—and sustain—this priority.
- Address any IT/audit staffing and resource shortages as well as a lack of supporting technology/tools, either of which can impede efforts to manage cyber security risk
Internal Audit Focus Areas
There are five key components crucial to cyber preparedness. Here’s how internal audit can contribute to each one:
Protection: Internal audit provides a holistic approach to identifying where an organization may be vulnerable. Whether testing bring-your-own-device (BYOD) policies or reviewing third-party contracts for compliance with security protocols, internal audit offers valuable insight into protection efforts. Having effective IT governance is also crucial, and internal audit can provide assurance services for that area as well.
Detection: Good data analytics often provide organizations the first hint that something is awry. Increasingly, internal audit is incorporating data analytics and other technology in its work. The 2015 CBOK practitioner survey found that five in 10 respondents use data mining and data analytics for risk and control monitoring, as well as fraud identification.
Business Continuity: Proper planning is important for dealing with and overcoming any number of risk scenarios that could impact an organization’s ongoing operations, including a cyber attack, natural disaster or succession.
Crisis Management/Communications: Preparedness in crisis management and crisis communications can significantly and positively impact an organization’s customers, shareholders and brand reputation. Internal audit can help with plan development, provide assurance checks of its effectiveness and timeliness, and ultimately offer analysis and critiques after plans are executed.
Continuous Improvement: Internal audit may provide the most value by contributing insight gleaned from its extensive scope of work. Cyber preparedness assumes survival of a cyber attack, but it serves no purpose if the organization does not evolve and improve its strategies and protocols to be better prepared for the next attack.
This information is further detailed in the Internal Audit’s Role in Cybersecurity Guide, including internal audit’s role with the board and example cyber security issues to look out for.
Other related resources on KnowledgeLeader:
- Manage Security and Privacy Risk Control Matrix (RCM)
- Managing Cyber Threats with Confidence
- User Information Security Policy
- 10 Tips for Companies to Raise Cyber Awareness Among Employees
- Infrastructure Policy: Incident Response
- Data Breach Notification Memo



